A long time ago, I used PGP for signing my email, but I stopped using it. Probably because I didn't quite get the concept yet, but that has changed now.
Today I switched to GPG for signing my mail and files, with all the required files running from my memory stick.
One thing bothered me however, no Outlook 2007 support at all. There are some plugins around for older Outlook versions, but that didn't quite work out.
So I decided to develop my own! And after a few weeks of development and testing, it's done and ready to be set free upon the world.
Let's have a look at the functionality and how to set it up and use it.
Prerequisites
First of all, a working copy of GPG is required, so visit the GnuPG download page, scroll down and download the command line Windows version.
Install this somewhere on your machine and remember the path where you installed it.
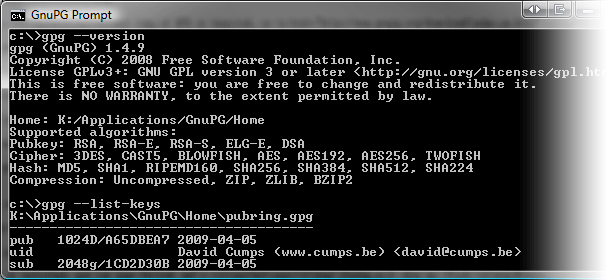
If everything has gone correctly, you can now open a command prompt and type gpg --version and gpg --list-keys to see the version and your keys (which would be empty if you're using it for the first time).
Visit the Getting Started section of the GnuPG handbook to generate your own key if this is your first encounter.
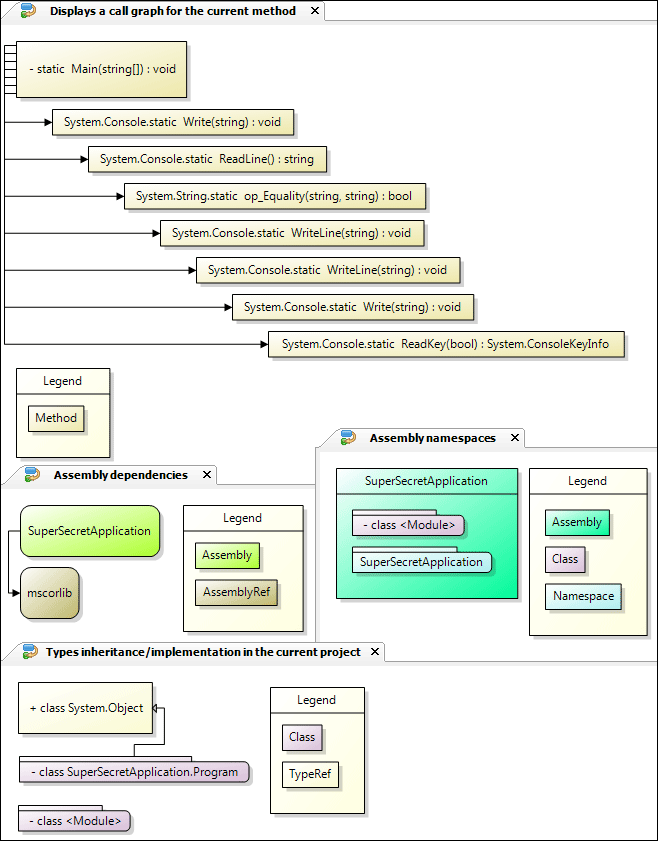
OutlookGnuPG
There are two main areas in the plugin, functionality for sending a mail (sign/encrypt) and for retrieving a mail (verify/decrypt).
At the moment only plain text emails are supported. No HTML mail or attachments, that's for a future version :)
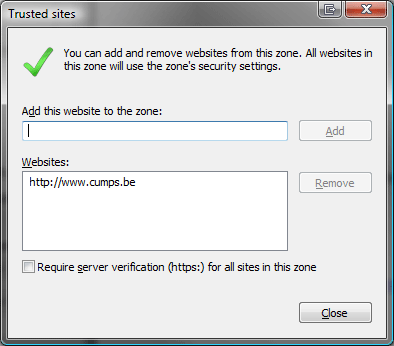
To install the addin, start by adding www.cumps.be to your Trusted Sites (you can do this in Internet Explorer - Tools - Internet Options - Security - Trusted Sites - Sites).
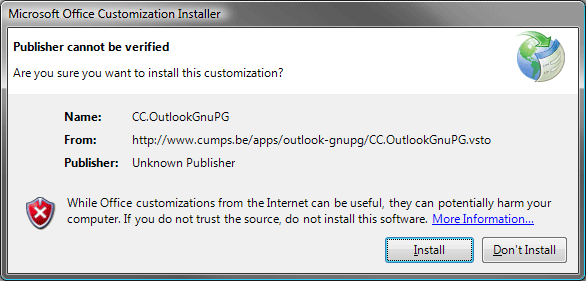
Download the OutlookGnuPG ClickOnce installer and execute it. (See Update 1 and 2 below)
This will give you a prompt asking you if everything is fine. Go ahead and install it. You might have to close Outlook before installing.
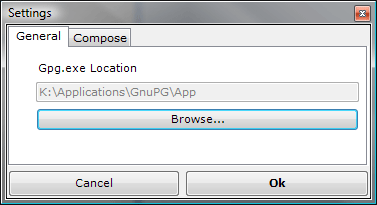
When the addin is installed, you can open Outlook and a Settings dialog will show up. Click Browse... and select the directory where your the gpg.exe you previously installed is located.
On the second tab you can select the default key you want to use to sign your mails. You will still have a choice to change your key upon sending the actual mail.
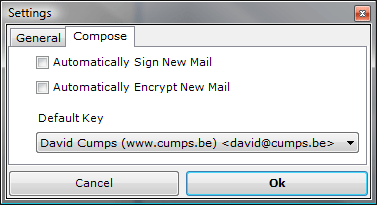
Click Ok when done. At this point you can use your Outlook as before, since we haven't checked any auto-sign/encrypt functionality.
Sending Mail
When you compose a new mail, you will notice the Message ribbon has a new group on it, called OutlookGnuPG, with a Sign and Encrypt toggle button.
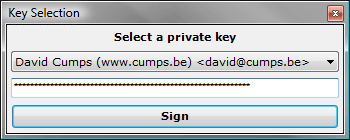
Sending out a signed mail is as simply as turning on the Sign button, typing your mail and pressing Send. It will prompt you to select the private key you want to use to sign the mail, and your passphrase.
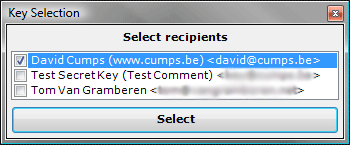
Creating an encrypted mail follows the same logic, toggle the Encrypt button and send your mail. You will have to select the intended recipients (multiple are possible) and it will encrypt the mail so only these people will be able to decrypt it.
To be absolutely safe, you can toggle both Sign and Encrypt button to send out an encrypted signed message.
Retrieving Mail
Reading mail can be done in two ways in Outlook, either by opening the mail item, or by using the preview pane. It only makes sense there are two ways to verify/decrypt a mail as well then.
The first is very identical to the send functionality. When you open an existing mail, you will notice a new ribbon group, OutlookGnuPG, with a Verify and Decrypt button.
Simply click Verify to check if a signed mail is valid or not. A messagebox will inform you of the status.
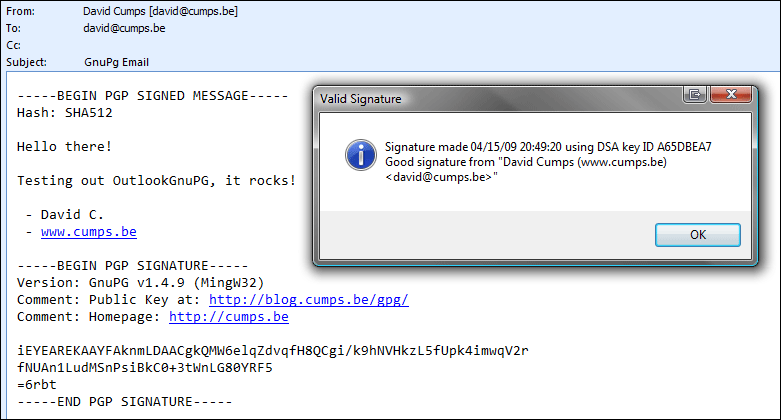
Likewise, click Decrypt to decrypt an encrypted email. This will ask you for your private key to decrypt the message with. The message will be decrypted, and the decrypted content will be placed in the message. If the message was also signed, a messagebox will inform you of the status.
The second way is through the preview window. A new commandbar will have appeared on the preview window, with a Verify and Decrypt button, which work exactly the same as the previous buttons.

Credits
OutlookGnuPG is free, only supported by a donate button, so it's only fair to give the used resources some credits.
Silk Icon Set by Mark James OpenPGP wrapper by Starksoft Clipboard Wrapper by Alessio Deiana
Feedback
Got questions? Remarks? Feel free to leave a comment :)
Update: Since I won't have the time to maintain this, I'm releasing the source: cc.outlookgnupg-1.0.8.0.zip
Update 2: Philippe Teuwen and Thierry Walrant have taken it upon themselves to improve the code I posted above and made it available on github, using GPLv3 as a license. Check it out at: github.com/twalrant/OutlookGnuPG